Week 2: Global Infrastructure and Reliability, Networking
Week two
two weeks of AWS…
high availability and fault tolerance.
choose a Region
Four key factors to choose a Region: Compliance, proximity, feature availability, and pricing.
- Compliance with data governance and legal requirements:Depending on your company and location, you might need to run your data out of specific areas.
- Proximity to your customers
- Available services within a Region: feature availability: Sometimes the closest Region may not have all the AWS features you want.
- Suppose that you are considering running applications in both the United States and Brazil. The way Brazil’s tax structure is set up, it might cost 50% more to run the same workload out of the São Paulo Region compared to the Oregon Region.
AZ
AWS calls a single data center or a group of data centers, an Availability Zone or AZ.Each Availability Zone is one or more discrete data centers with redundant power, networking, and connectivity.
AWS(Amazon Web Services)的基础架构设计:如何设计和实现其Regions和Availability Zones (AZs)以确保高可用性和容灾能力。简言之,AWS鼓励在多个AZs中运行应用,以确保即使一个AZ受到影响,应用仍然可以正常运行。
关于您的问题:“所以是不是同一个服务最好买2个ec2?”的答案是:
是的,为了确保高可用性和容错能力,您应该考虑在至少两个不同的Availability Zones中运行两个或更多的EC2实例。这样,如果一个AZ发生故障或受到影响,其他的AZ中的实例仍然可以为用户提供服务。这不仅增加了冗余,而且还提供了容灾和故障恢复能力。
Running Amazon EC2 instances in multiple Availability Zones
AZ & Region
在AWS(Amazon Web Services)的上下文中,一个单独的数据中心或一个区域内的一组数据中心被称为”Availability Zone”(常简称为AZ)。
**Availability Zone (AZ)**:这是AWS基础设施的一个关键部分,用于提供高可用性和容错能力。
- 一个AZ可以是一个单独的数据中心,也可以是一个地理区域内的几个物理上接近的数据中心。
- 每个AZ都有独立的电源、网络、冷却系统等,从而确保它可以在其他AZs出现问题时独立运行。
- 不同的AZs之间有低延迟的网络连接,从而确保在一个AZ内的资源可以与另一个AZ内的资源快速互相通信。
Region:一个Region是AWS全球基础设施的一个地理区域。每个Region都包括两个或多个Availability Zones。
- For example, the South America (São Paulo) Region is sa-east-1. It includes three Availability Zones: sa-east-1a, sa-east-1b, and sa-east-1c.
- 选择不同的Regions可以帮助您满足法规要求、降低延迟或提供距离用户更近的服务。
为了提供高可用性和容错能力,AWS鼓励用户在一个Region的多个AZs中分布式部署他们的应用和服务。这样,如果一个AZ出现问题,其他AZs仍然可以继续为用户提供服务。
Edge Locations:
An edge location is a site that Amazon CloudFront uses to store cached copies of your content closer to your customers for faster delivery.
“Edge Locations” 和 “regional zone” 是两个不同概念,分别指代了 AWS 中的不同部分。
Edge Locations(边缘位置): 这是 Amazon CloudFront CDN(内容分发网络)的一部分。Edge Locations 是分布在全球各地的服务器节点,用于将内容和数据缓存在距离用户更近的位置,以提供更快速、高效的内容分发。Edge Locations 位于多个城市,用于加速内容传输并减少延迟。它们并不是 AWS 云基础设施的一部分,而是为了加速内容分发而存在的。
Regional Zone(区域性区域): 在 AWS 基础设施中,一个区域(Region)代表了一个地理上的独立数据中心集合,每个区域都由多个可用区(Availability Zones)组成。每个可用区是一个独立的数据中心,通常位于一个区域内的不同地理位置,以提高可用性和冗余性。一个区域可以包括多个可用区,以支持高可用性和灾难恢复。
总结来说,Edge Locations 是用于内容分发的服务器节点,而 Regional Zone 是 AWS 云基础设施中的一部分,用于实现高可用性和冗余性。
- They run a domain name service, or DNS, known as Amazon Route 53, helping direct customers to the correct web locations with reliably low latency.
- Introducing AWS Outposts, where AWS will basically install a fully operational mini Region, right inside your own data center. That’s owned and operated by AWS, using 100% of AWS functionality, but isolated within your own building.
Here’s the key points. Number one, Regions are geographically isolated areas, where you can access services needed to run your enterprise. Number two, Regions contain Availability Zones, that allow you to run across physically separated buildings, tens of miles of separation, while keeping your application logically unified. Availability Zones help you solve high availability and disaster recovery scenarios, without any additional effort on your part, and number three, AWS Edge locations run Amazon CloudFront to help get content closer to your customers, no matter where they are in the world.
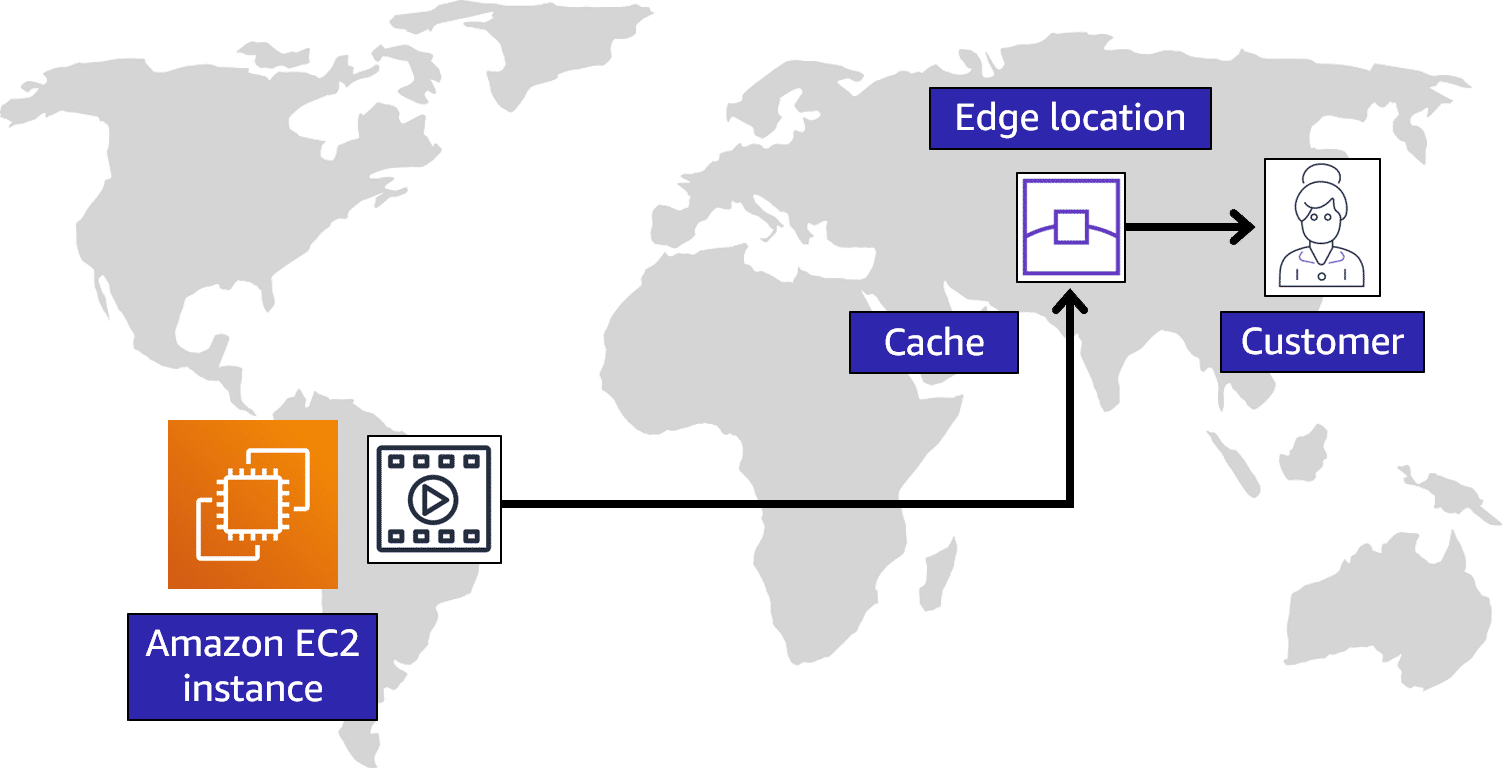
When a customer in China requests one of your files, Amazon CloudFront retrieves the file from the cache in the edge location and delivers the file to the customer. The file is delivered to the customer faster because it came from the edge location near China instead of the original source in Brazil.
How to Provision AWS Resources
For example, you can launch an EC2 instance or you can create an AWS Lambda function. Each of those would be different requests and different API calls to AWS.
You can use the AWS Management Console, the AWS Command Line Interface, the AWS Software Development Kits, or various other tools like AWS CloudFormation, to create requests to send to AWS APIs to create and manage AWS resources.
Interacting with AWS:
- AWS Management Console
- CLI
- SDKs
- AWS Elastic Beanstalk
- AWS CloudFormation
Provisioning a resource:
- Log in to the AWS Management Console
- Write commands
- Write programs
By using AWS Command Line Interface (AWS CLI) we don’t need to perform operations in web user interface of AWS, instead we can send command programmatically through our application to speed up processes.
Manage tools:
AWS Elastic Beanstalk and AWS CloudFormation
AWS Elastic Beanstalk 适用于简化 Web 应用程序的部署和扩展,而 AWS CloudFormation 则适用于以代码方式管理复杂基础设施的情况。
AWS Global Infrastructure:
Availability Zones
Regions
Deploy infrastructure across at least 2 Availability Zones
Edge locations
AWS Outposts
Summary:
AWS Outposts is a service that enables you to run infrastructure in a hybrid cloud approach.
AWS Fargate is a serverless compute engine for containers.
Amazon CloudFront is a content delivery service.
AWS Outposts can extend AWS infrastructure and services to your on-premises data center.
The AWS Command Line Interface (AWS CLI) is used to automate actions for AWS services and applications through scripts.
The AWS Management Console includes wizards and workflows that you can use to complete tasks in AWS services.
Software development kits (SDKs) enable you to develop AWS applications in supported programming languages.
Interactive map of the AWS Global Infrastructure
AWS Networking and Content Delivery Blog
Networking
Amazon Virtual Private Cloud (Amazon VPC)
These resources can be public facing so they have access to the internet, or private with no internet access, usually for backend services like databases or application servers. The public and private grouping of resources are known as subnets and they are ranges of IP addresses in your VPC.
VPC lets you provision a logically isolated section of the AWS Cloud where you can separate resources you want to be public from private. That way we can place resources as part of a public subnet while others remain on the private subnet.
VPC(Virtual Private Cloud)是 AWS 中的一个服务,用于创建一个逻辑隔离的虚拟网络环境。在这个虚拟网络环境内可以定义自己的 IP 地址范围、子网、路由表、安全组等网络设置,并将 AWS 资源部署在其中。
If you want to establish an encrypted VPN connection to your private internal AWS resources, you would need to attach a virtual private gateway to your VPC.虽然 VPN 连接是私密的且加密的,但它们仍然使用共享的互联网连接,可能会受到互联网流量拥塞和影响。
Direct Connect allows you to establish a completely private, dedicated fiber connection from your data center to AWS.这是一种能够在数据中心与 AWS 之间建立私有、专用的光纤连接的服务。它提供了物理连接,旨在满足高规制和合规性需求,避免带宽问题。
It’s also important to note that one VPC might have multiple types of gateways attached for multiple types of resources all residing in the same VPC, just in different subnets.
子网(Subnet)是在一个大型网络中划分出的较小的、逻辑上隔离的网络分区。在计算机网络中,子网的存在允许网络管理员更有效地管理和组织 IP 地址,同时也有助于提高网络的性能、安全性和可管理性。
在 AWS 中,子网是在虚拟私有云(VPC)内部划分出的一块 IP 地址范围,用于将 VPC 进一步分隔成更小的网络区域。每个子网可以关联一个特定的可用区(Availability Zone),使得资源可以在特定的地理位置部署。
子网是网络中划分的较小的区域,它允许更好地管理 IP 地址、资源组织和访问控制,尤其在 AWS 的 VPC 中,子网有助于更好地利用和配置资源。
- IP 地址范围: 每个子网有一个自己的 IP 地址范围,它是从 VPC 的 IP 地址范围中分配的一部分。
- 隔离性: 子网之间是隔离的,这意味着位于不同子网中的资源不能直接通信,除非在 VPC 级别的网络访问控制规则中允许。
- 关联可用区: 每个子网可以关联到一个特定的可用区,这使得您可以在不同的地理位置部署资源,从而提高可用性和容错性。
- 公共和私有访问: 通过适当配置路由表和网络访问控制列表,您可以控制子网中资源的公共或私有访问性。
- 资源分组: 子网允许您根据需要将资源组织在一起,例如将公共资源放在一个子网,将私有资源放在另一个子网。
VPC(Virtual Private Cloud),VPN(Virtual Private Network),以及 VPS(Virtual Private Server)都是与虚拟化和网络相关的概念,但它们在 AWS 和计算领域中具有不同的含义和用途。
VPC(Virtual Private Cloud):
- VPC 是 Amazon Web Services(AWS)提供的一种虚拟网络服务。它允许您在 AWS 云中创建一个逻辑隔离的网络环境,类似于在云上构建自己的专用数据中心。
- VPC 可用于创建子网、路由表、安全组等,使您可以控制网络配置、资源隔离和安全性设置。
- 主要用途是在 AWS 云中创建自定义的网络拓扑,将资源划分为公共子网和私有子网,实现安全且可管理的网络环境。
VPN(Virtual Private Network):
- VPN 是一种网络技术,用于在公共网络上创建一个加密的、安全的连接,以连接远程地点或用户到私有网络。
- VPN 允许用户在 Internet 上建立安全通信通道,使远程用户、分支机构等能够安全地访问私有网络内的资源。
- 主要用途是实现远程访问和安全通信,通常用于将分散在不同地点的网络连接起来。
VPS(Virtual Private Server):
- VPS 是一种虚拟服务器,它是在物理服务器上通过虚拟化技术创建的一个独立的虚拟服务器实例。
- VPS 允许用户拥有一个类似于物理服务器的虚拟环境,可以安装操作系统、应用程序和服务。
- 主要用途是为个人或企业提供经济实惠的服务器托管解决方案,允许用户获得独立的计算资源和控制权。
总结来说,VPC 是 AWS 提供的虚拟网络服务,VPN 是网络技术用于加密连接,VPS 是虚拟服务器实例,每个概念都在不同的层面解决了虚拟化和网络需求。
Connectivity to AWS
To allow public traffic from the internet to access your VPC, you attach an internet gateway to the VPC.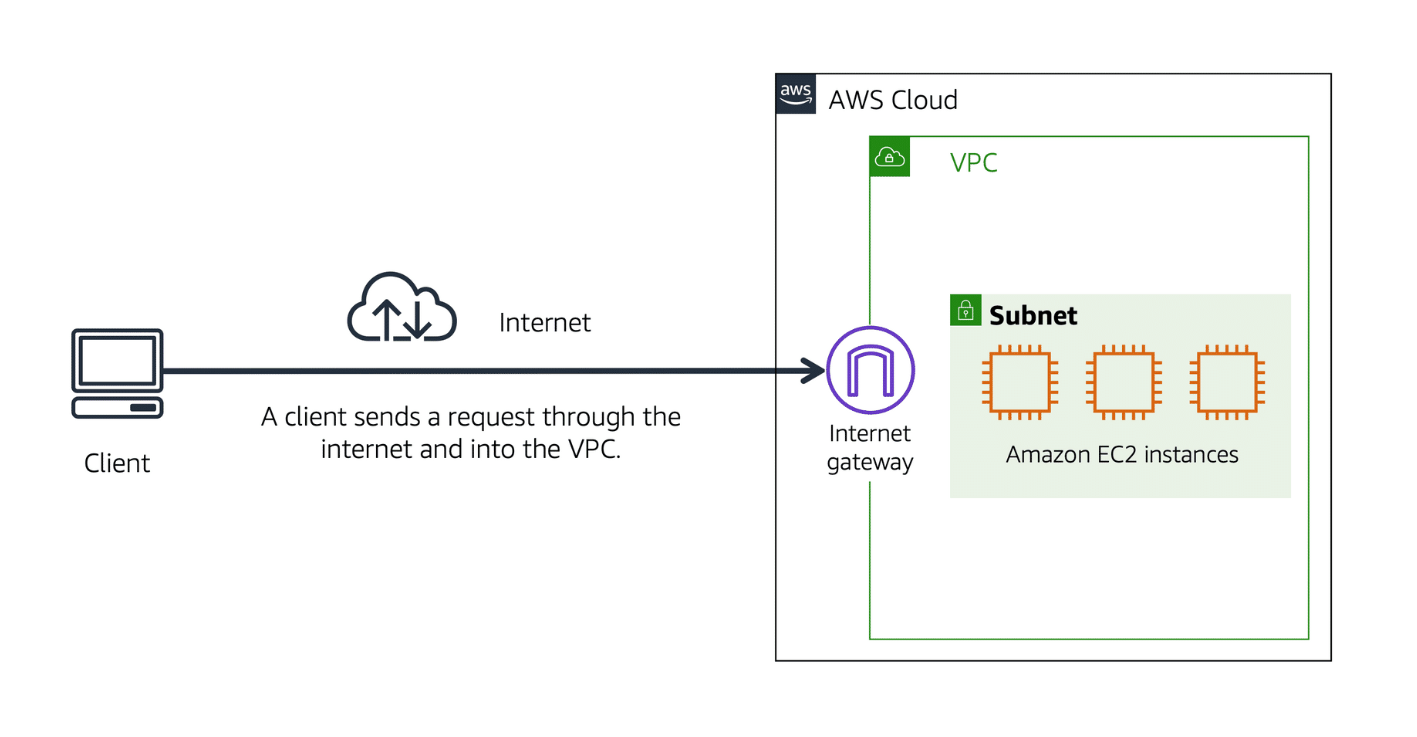
关于AWS网络连接和Amazon Virtual Private Cloud(Amazon VPC):
Amazon VPC是AWS提供的网络服务,用于在AWS云中创建隔离的虚拟网络环境,以将资源组织成子网,并为资源之间建立边界。
Internet Gateway是连接VPC和互联网的组件,允许公共流量从互联网访问VPC。
如果您的VPC只包含私有资源,可以使用Virtual Private Gateway建立虚拟私有网络(VPN)连接,以加密和保护互联网流量。
AWS Direct Connect是一项服务,可为您的数据中心和VPC之间建立专用的私有连接,类似于一个专用的走廊,只允许特定的流量通过,以降低网络成本并增加带宽。
总的来说,Amazon VPC、Internet Gateway、Virtual Private Gateway和AWS Direct Connect是AWS提供的工具和服务,用于建立和管理AWS资源之间的网络连接,确保网络流量的安全和有序传输。这些工具允许客户在AWS云中创建高度定制的网络架构,以满足其特定的需求和安全要求。
AWS的网络硬化(Network Hardening)是一种网络安全实践,旨在增强Amazon Web Services(AWS)云环境的网络安全性。网络硬化措施有助于减少潜在的网络攻击面,提高网络基础设施的安全性,从而降低潜在威胁和风险。以下是一些常见的AWS网络硬化实践和策略:
安全组和网络访问控制列表(ACLs):配置安全组和网络ACLs,以限制网络流量的访问权限。只允许必要的流量通过,并拒绝不必要或不受信任的流量。
子网隔离:使用Amazon VPC(Virtual Private Cloud)创建多个子网,将不同的应用程序或服务隔离开来。这有助于限制横向扩展攻击的影响。
VPN和Direct Connect:使用虚拟专用网络(VPN)或AWS Direct Connect建立安全的远程连接,以保护数据在云和本地数据中心之间的传输。
安全通信:启用HTTPS和TLS等协议来保护数据在传输过程中的机密性。使用AWS证书管理服务来管理SSL/TLS证书。
网络监控和审计:使用AWS CloudWatch、AWS CloudTrail和其他监控工具来实时监控网络活动和审计日志,以便及时检测和应对潜在的安全威胁。
安全策略:制定并实施网络安全策略,包括强密码政策、多因素身份验证(MFA)、访问控制策略等。
自动化:利用AWS的自动化工具和服务,如AWS Identity and Access Management(IAM)策略、AWS Config规则等,自动执行安全策略和修复操作。
更新和漏洞管理:定期更新操作系统、应用程序和AWS服务,以修复已知漏洞,并监控CVE(通用漏洞和漏洞)通知以获取新漏洞的信息。
安全培训和教育:培训团队成员,使他们了解网络安全最佳实践,并提高对潜在威胁的识别能力。
安全组和网络访问控制列表(ACLs):
安全组-stateful
网络访问控制列表-stateless
VPC里有Subnet,Subnet里有EC2;Internet Gateway是VPC的入口,ACL是Subnet的,安全组是EC2的。。。
The public subnets have access to the internet gateway; the private subnets do not. But subnets can also control traffic permissions. Packets are messages from the internet, and every packet that crosses the subnet boundaries gets checked against something called a network access control list or network ACL. This check is to see if the packet has permissions to either leave or enter the subnet based on who it was sent from and how it’s trying to communicate.
ACL only gets to evaluate a packet if it crosses a subnet boundary, in or out. It doesn’t evaluate if a packet can reach a specific EC2 instance or not. Sometimes, you’ll have multiple EC2 instances in the same subnet, but they might have different rules around who can send them messages, what port those messages are allowed to be sent to. So you need instance level network security as well. To solve instance level access questions, we introduce security groups.
Every EC2 instance, when it’s launched, automatically comes with a security group. And by default, the security group does not allow any traffic into the instance at all. All ports are blocked; all IP addresses sending packets are blocked.
If NACLs are a passport control, a security group is like the doorman at your building.The doorman will check a list to ensure that someone is allowed to enter the building but won’t bother check the list on the way out. With security groups, you allow specific traffic in and by default, all traffic is allowed out.
网络访问控制列表(Network ACLs)类似于护照控制官,用于检查流量是否有权限进入或离开子网。它们是无状态的,每个包都会受到检查。
安全组(Security Groups)类似于建筑物的门卫,用于控制特定EC2实例的流量,可以允许特定类型的流量进入实例,同时默认情况下允许所有流量离开实例。
安全组是有状态的,它们记住先前允许的流量,因此在返回流量时不需要重新检查。
网络ACL和安全组一起使用,以实现网络深度安全,以确保对资源的流量具有多层次的保护。
Security groups operate at the AWS network level, not at the EC2 instance level, like an operating system firewall might.
In a VPC, subnets are separate areas that are used to group together resources.
NACL
Which statement best describes an AWS account’s default network access control list?
It is stateless and allows all inbound and outbound traffic.
Network access control lists (ACLs) perform stateless packet filtering. They remember nothing and check packets that cross the subnet border each way: inbound and outbound.
Each AWS account includes a default network ACL. When configuring your VPC, you can use your account’s default network ACL or create custom network ACLs.
By default, your account’s default network ACL allows all inbound and outbound traffic, but you can modify it by adding your own rules. For custom network ACLs, all inbound and outbound traffic is denied until you add rules to specify which traffic should be allowed. Additionally, all network ACLs have an explicit deny rule.
This rule ensures that if a packet doesn’t match any of the other rules on the list, the packet is denied.
Learn more: https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html
Route 53 和 Amazon CloudFront
Amazon Route 53: 这是AWS的域名系统(DNS)服务,用于将网站域名转换为与之关联的IP地址。它的名称中的 “Route 53” 指的是端口 53,这是用于 DNS 的默认端口。DNS就像一个翻译服务,它将用户输入的网站地址翻译成计算机可读的IP地址。Route 53不仅高可用和可扩展,还可以根据不同的路由策略将流量定向到不同的终端点,如基于延迟的路由、地理位置DNS、地理位置近似和加权轮询。
Amazon CloudFront: 这是AWS的内容分发网络(CDN)服务,用于加速网站资产(如图像、GIF等)的交付给用户。CloudFront通过在全球范围内部署边缘位置来提供内容,以使用户能够从距离他们最近的位置获取内容。这有助于改善网站性能,减少延迟。
CDN(内容分发网络): CDN是一个网络,根据用户的地理位置将内容交付给他们,从而提高内容交付的速度和效率。通过将静态网站资产部署在CloudFront的不同区域,可以确保用户从最近的位置获取这些资产,从而改善用户体验。
Summary
With AWS, networking is now simplified and abstracted to answer the simple question of who should be allowed to communicate with each other.
VPC (Virtual Private Cloud): AWS’s virtual network environment for isolating and organizing workloads.
Network Security Fundamentals: Basics of network security, including gateways, Network ACLs, and security groups.
Connecting to AWS: Methods for establishing connections to AWS resources, like VPN and Direct Connect.
Global Network and Edge Locations: AWS’s global network infrastructure with edge locations for faster content delivery.
Route 53 and DNS: AWS’s DNS service (Route 53) for translating domain names into IP addresses.
CloudFront and Content Caching: AWS’s CDN service (CloudFront) for caching and delivering static content.
Quiz
(Private subnet, DNS, AWS Direct Connect, Virtual private gateway): Which component can be used to establish a private dedicated connection between your company’s data center and AWS? - AWS Direct Connect
Which statement best describes security groups? - Security groups are stateful and deny all inbound traffic by default.
Which component is used to connect a VPC to the internet? - Internet gateway.